As some others unix-like operating systems FreeBSD has some particularities aside to the UNIX heritage, licensing and the like. The init system is the way a system starts up and the BSD has always been different. If you happen to be a UNIX admin I am sure you are aware of this and the folks […]
FreeBSD particularities

How to update FreeBSD using beadm
Beadm is a tool which provides a wonderful and distinctive functionality on Solaris, OpenIndiana and FreeBSD. It relies on the ZFS filesystem allowing to take a filesystem snapshot. That can be used to manage the so called boot environments which provide a great way to secure updates, even when everything goes down the tubes. Hence […]
How to install Suricata on FreeBSD
Suricata is a free, open source, Intrusion Detection System software, or IDS for short. But it can also act as an Intrusion Prevention System, or IPS. It works by finding patterns using heuristics typically from network traffic. When configured to just warn about suspicious activity it is called an IDS, however when it blocks the […]
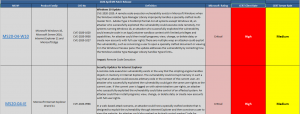
Microsoft’s Patch Tuesday – April 2020
For the first time here at adminbyaccident.com I will share some information about Windows patching that I hope can shed some light and help people on deciding what to patch and how quickly to patch. Digesting Microsoft’s Patch Tuesday releases is always tricky. The amount of information is overwhelming and since almost every company on […]
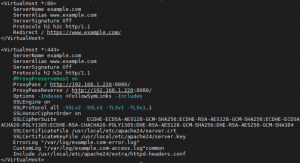
How to configure Apache HTTP as a reverse proxy on FreeBSD
Apache HTTP as a reverse proxy consists on setting an Apache HTTP server as a frontal access for one or multiple backend servers. In the recent years many have started using NGINX as a reverse proxy since this piece of software really shines for serving static content an acting as a cache server. This doesn’t […]

How to install software in FreeBSD with pkgng
The pkgng is the package management system in FreeBSD. It is used to install applications, and specific modules, libraries, etc. Nowadays you can select in between more than 25.000 thousand. Yes, twenty five thousand. The syntax to use is very intuitive and simple. As you may be already aware software comes in two forms. Source […]
How to load and unload kernel modules in Linux
Kernel modules permit enabling hardware features on a given system. For example, if we need to read from a particular filesystem from a hard drive, we need to load a particular kernel module. Or use a specific network card, a sound card or sound device, a video display, etc. This is mostly done automatically in […]

A brief introduction to SSL/TLS certificates
SSL stands for Secure Sockets Layer and it an old implementation of a crytographic protocol. TLS, or Transport Layer Security, is a new one. They are both used to have privacy in the communications between different parties. They are used to secure email, web browsing, instant messaging, etc These protocols work in a complex way […]
How to install Ansible on FreeBSD
Ansible is a very useful tool geared to system’s configuration and applications deployment. In this how to install Ansible on FreeBSD I will briefly explain what the tool is, what it does, what it does not and how to install it on FreeBSD. I will also demonstrate very basic use and on a later article […]

How to install the Clamav antivirus in FreeBSD
Clamav is an antivirus. But don’t think of Clamav as the antivirus you have sitting in your personal computer at home or in your office. It’s an antivirus that works under user demand. It is not constantly monitoring the system. So you will have to setup some cronjobs in order to check and monitor the […]