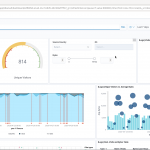
The ELK stack stands for Elasticsearch, Logstash and Kibana. These three pieces of software are very useful since each brings a powerful capability that in combination is just great to use. Elasticsearch is a search and analytics engine. Logstash can process data from multiple sources. Kibana allows to visualize data in a graphic manner. These three capabilities combined is … [Read more...]
Archives for April 2020
How to install OSSEC agents on Windows
On a recent post I published about how to install an OSSEC server on Ubuntu I explained how this solution can help secure an infrastructure by deploying agents which report back to a central server. This is the second part of this server-client story. On this guide you will read about setting up agents and keys on the server side and how to install the agents on the client … [Read more...]
Exploiting CVE-2019-0708 Remote Desktop Protocol on Windows
The CVE-2019-0708 is the number assigned to a very dangerous vulnerability found in the RDP protocol in Windows sytems. This is also known as the ‘Blue Keep’ vulnerability. The issue was so critical that Microsoft did even release patches to unsupported operating systems such as Windows XP or Server 2003. To this day there are still thousands of devices around the world … [Read more...]
Microsoft’s Patch Tuesday – April 2020
For the first time here at adminbyaccident.com I will share some information about Windows patching that I hope can shed some light and help people on deciding what to patch and how quickly to patch. Digesting Microsoft’s Patch Tuesday releases is always tricky. The amount of information is overwhelming and since almost every company on earth is relying on a fair amount of … [Read more...]
Web credentials stealing
The theft of credentials has been occurring since almost the beginning of time. But of course when the web ‘happened’ and specially when e-commerce exploded stealing passwords also went on the rise. Emptying bank accounts, ordering stuff on behalf (and expenses) of others, spying, even impersonation was and is achieved by stealing credentials. Luckily for us identity got … [Read more...]