For the first time here at adminbyaccident.com I will share some information about Windows patching that I hope can shed some light and help people on deciding what to patch and how quickly to patch.
Digesting Microsoft’s Patch Tuesday releases is always tricky. The amount of information is overwhelming and since almost every company on earth is relying on a fair amount of software from them, security teams struggle to gather all the information and make it pallatable, understandable for everyone. Crucially deciding what cadence of patch and filtering out what is urgent from what isn’t is the cornerstone of updating systems.
Anyone can download an Excel spreadsheet I’ve prepared with some relevant information about patching for this April’s Patch Tuesday 2020.
If you find the articles in Adminbyaccident.com useful to you, please consider making a donation.
Use this link to get $200 credit at DigitalOcean and support Adminbyaccident.com costs.
Get $100 credit for free at Vultr using this link and support Adminbyaccident.com costs.
Mind Vultr supports FreeBSD on their VPS offer.
To understand this file I’ve prepared a short guide.
Cadence:
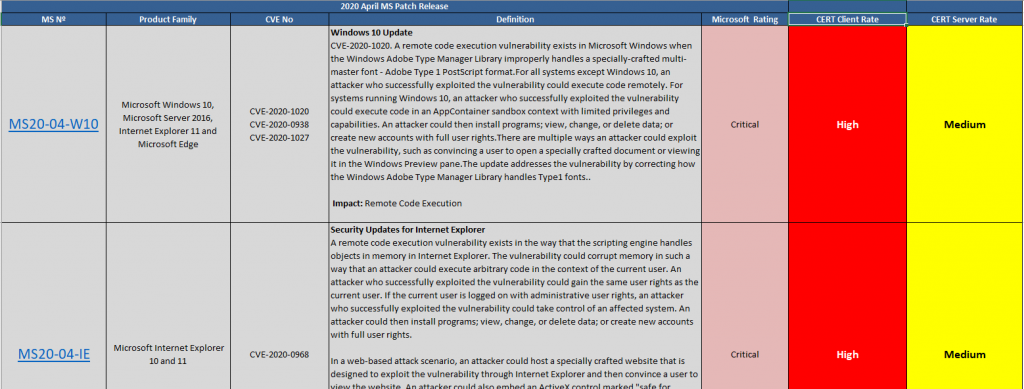
The patching cadence is marked on the right two columns and spans like follows:
– Critical: Patch under 7 days
– Hight: Patch under 30 days
– Medium: Patch under 60 days
– Low: Patch under 90 days
The two columns are relevant since they divide software between Client and Server. For example, Office is not typically found on any server, but it will on almost every Workstation. Inevitably Internet Explorer is installed on every system, and although a vulnerability may be tipified as ‘High’ for client devices it won’t be necesseraly qualified the same on servers. This is due to servers not usually having direct internet access nor any real external browsing capacity. At least they shouldn’t.
The file does also contain tabs at the bottom so every product or family of products is contained.
![]()
Sources:
All the information gathered in this document and the Excel spreadsheet has been extracted from the official Microsoft’s site. For further investigation you can use the following link.
https://portal.msrc.microsoft.com/en-us/security-guidance
Scope:
The scope found on the file is limited to those products found on almost every company. Some bits like, for example, Exchange are not found this month due to no vulnerabilities have been disclosed around it. Development tools such as Visual Studio are out of the scope.
However the Excel file does not collect information for discontinued releases of Microsoft Windows, although some vulnerabilities may or may not apply to those systems as well.
Evaluation criteria:
The value of any given vulnerability is addressed by the vendor using the CVSS version 3.0 scale. Microsoft does also use and publish their Explotability Assessment for each vulnerability.
On the other hand I have applied my own professional criteria to sort out the cadence of the patching on a general basis. Adjuts this to your environment if you choose the follow this document as a resource.
Relevant for this April’s Patch Tuesday:
Be aware! The more critical vulnerabilities for this April’s Patch Tuesday do also apply for older, discontinued versions of Windows. Be sure you are either upgrading systems to current versions or you have a contract with Microsoft or other third party vendor to obtain licenses for the Extended Security Updates program.
The highlights for this month:
Affecting all supported and unsupported operating sytems:
CVE-2020-1020 and CVE-2020-0938 go in tandem since they apply to the same software, both are critical and the exploitation leverages the same component, this being the Adobe Font Manager Library. The issue resides on how the library manages Adobe Type 1 PostScript format. A specially-crafted font could trigger these remote execution vulnerabilities. More importantly these have already been detected being exploited in the wild. The more plausible scenario consists of an attacker crafting a document and tricking users to open it.
Furthermore CVE-2020-1027, a Windows kernel elevation of privilege vulnerability does also stand out among the 113 issues listed. There is little detail on this one but the premise is a deffect on how the Windows kernel handles objects in memory. As a result remote code execution is possible gaining elevated privileges too. The attack must be performed by an already authenticated user running a specially designed program.
Microsoft Dynamics:
The CVE-2020-1022 hasn’t been included on the Excel spreadsheet, since not all businesses are using it but it has been assigned critical severity. The vulnerability allows remote code execution, in this particular case running shell commands. To exploit this the malicious actor, must be already authenticated and must convince a user to connect to a malicious Dynamics Business Central Client or elevate permission into the sytem to execute commands.
Microsoft Graphics Components:
The Graphics Components has also got its share of vulnerabilities spanning from ‘Important’ to ‘Critical’ qualifications. On top of this stack of issues the CVE-2020-0687 has been given a base score of 8.8 and has been assigned a ‘criticial’ grade, as well as it has CVE-2020-0907. The former is related on how the Windows font library handles specially crafted fonts. The latter can be summarized on issues on how the Graphics Componentes handle objects in memory.
Hyper-V:
On the Hyper-V virtualization front CVE-2020-0910 arises as a critical issue on how a host server fails to validate input from an authenticated user on a guest OS. The user on the guest OS could run a specially crafted program to run arbitrary code on the host. It’s been given a base score of 8.4.
Office:
A series of remote code execution vulnerabilities have been addressed on this April’s Patch Tuesday, more specific details of these on the Excel spreadsheet.
Sharepoint:
Three vulnerabilities, among the 21 detail on the Excel sheet, should be taken care up front. There are a couple of Cross-Site Scripting (XSS) around and those trick the system by spoofing web requests and sneaking in. Though it looks like the attacker should’ve been priorly authenticated. Critical are CVE-2020-0931 and CVE-2020-0929 since they consist on RCE possibly affecting the whole pool of servers running Sharepoint.
Recommendations:
Patch. Just patch. Do please apply the patches.
Deploy solutions for distribution of patches avoiding the use of VPN. The throughput of the networks these days, where many workers are quarantined due to COVID-19, can exceed the capacity of your networks. It’s much easier to use the end user network to get these patches and avoid tunneling all this traffic through your VPN. Cloud solutions and GPOs can help on this particular enormously.
Make sure you are protecting discontinued versions of Windows, no matter what you have already set up to complement the security of those environments. Contact Microsoft of your favourite partner to obtain an ESU license.
Conclusion:
This is all for this April’s Patch Tuesday, hope this helps some users, administrators or IT people.
If you find the articles in Adminbyaccident.com useful to you, please consider making a donation.
Use this link to get $200 credit at DigitalOcean and support Adminbyaccident.com costs.
Get $100 credit for free at Vultr using this link and support Adminbyaccident.com costs.
Mind Vultr supports FreeBSD on their VPS offer.