As recently announced in a previous article I wanted to write a couple of guides on how to mitigate Spectre and Meltdown vulnerabilities in GNU/Linux and UNIX environments. It is always a good and I hope a standard practice to have your systems patched and if they aren’t for whatever the reason (that legacy thing […]

How to mitigate Spectre and Meltdown on a Lenovo T430s with FreeBSD
How to install Fail2ban on FreeBSD
Fail2ban is a complementary tool to your firewall. It works by scanning log files and bans IPs which present suspicious activity such as failed logins. It is compatible with many UNIX-like systems and is a security tool to have in your arsenal. It can filter not only ssh logins, but other services too, for example […]

How to install Drupal 9 on FreeBSD 13.0
Drupal 7 is approaching its original EOL (End of Life) date (Nov. 2021) which has been extended to November 2022 due to COVID’s impact. Most companies are using Linux already and have their upgrade plans in the works or are thinking about them. This is a good time to switch platform and use Drupal 9 […]

How to manually update Letsencrypt certificates on FreeBSD
Update 05-2020: If anyone is interested on the automatic process you can read my tutorial on DigitalOcean about the topic. On this guide we will manually update our Letsencrypt certificate on FreeBSD for a single website. It is a simple operation that can be automated as a cron job, but seeing it is always informative […]
VMWare ESXi (One)
The VMWare ESXi is a hypervisor developed by the VMWare company and it is widely known and used in many environments and enterprises of all sorts. Nowadays it is the main component of a sort of a software suite. It is a type one hypervisor which means it runs directly on to the hardware controlling […]
SSH keys
SSH or how to remotely control a UNIX system in a secure manner. The SSH keys is a secure method to interact with a UNIX system remotely. They are also used to transfer data between different systems. Using clever cryptography anyone can use them. As their name state it is a pair of keys, one […]

How to install Nessus 10 on FreeBSD 12
Nessus is a professional vulnerability scanner from the reputable cybersecurity company Tenable. I have already written about it in the past but installing it on a GNU/Linux distro. This very article will guide anyone to install Nessus 10 on FreeBSD, since Tenable is releasing binaries for FreeBSD 11 and 12 as of the time of […]

The Original Sin
Disclaimer: What you are about to read may contain inaccuracies. Feel free to discuss them somewhere else. This is also my opinion and as such it may change through time, maybe tomorrow, next month, next year, next decade or never. I do also make very few reviews (if any) of what I write here so […]
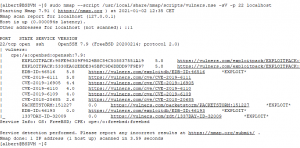
How to patch OpenSSH in FreeBSD 12.2
The default version of OpenSSH in FreeBSD 12.2 today, and it’s been this for quite some time, is not the most recent published by the OpenBSD guys, which by the way are the ones developing OpenSSH. Not only is not the latest but it has a few vulnerabilities affecting it, medium risk ones but nevertheless […]
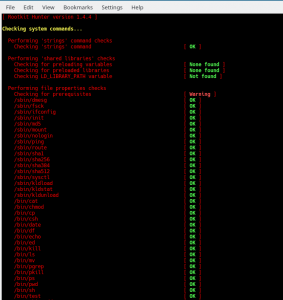
How to install RKHunter on FreeBSD
In this post you will find simple instructions to install rkhunter on FreeBSD which is a root kit “hunter” so your system/s will have some security in place for that kind of unwanted software. But for those who do not know what a rootkit is, let’s give it a simple definition (which you can get […]