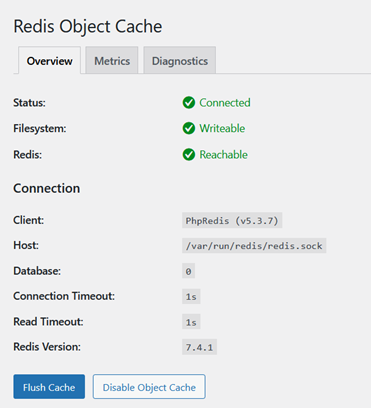
Having all the data in just one server is not the best idea. Especially when talking about a database server. Spreading information in several boxes is a good measure to prevent data loss but also for performance. A MySQL/MariaDB master-slave replication scheme is often used as a good solution for both, data redundancy and speed. […]
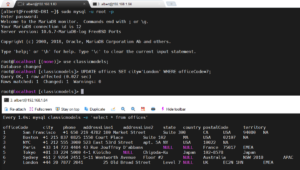
How to setup MariaDB master-slave replication on FreeBSD

How to secure FreeBSD (server minimal edition)
This is a very simple and easy to follow guide on securely administer your FreeBSD server. That said I am not a security expert although I’ve gained some knowledge as time goes by. Not pretending to be the definitive guide this article is an introduction on how to secure FreeBSD in which I will tackle […]
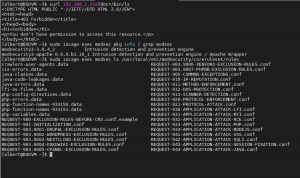
How to configure Modsecurity 3 for WordPress on FreeBSD
A few weeks ago I wrote a guide on how to install Modsecurity 3 on Apache HTTP for the FreeBSD operating system. However there’s a catch with that setting and with Modsecurity in general. As good as it is as a WAF you need to at least adjust its configuration to the tool one pretends […]

A brief introduction to Regular Expressions
A regular expression is a set of characters, a string of characters if you will, that specify a pattern. Ever used the grep command? It makes use of them. The ‘grep’ command is very handful when one needs to look for certain things inside a text file, or looking for some specific pattern from another […]

How to install the FAMP stack
You may have heard of the LAMP stack which stands for Linux, Apache, MySQL and PHP or Perl. This is the same but instead of using the GNU/Linux operating system we’ll use FreeBSD. This is the FAMP stack. There are two ways to install software in FreeBSD, packages and the ports collections. Which in the […]
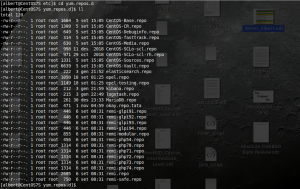
How to set CentOS 7 repositories
CentOS is the free open source replica of the well known Red Hat Enterprise Linux (RHEL). With a very good reputation because of its stability and performance RHEL is nowadays the dominating GNU/Linux distribution in the enterprise environment. As a gift, in a similar fashion to Microsoft’s Windows trial versions (without limits to the use), […]
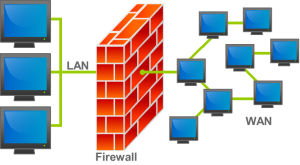
The firewall
If you don’t know why you need a firewall it’s because you are not very tech savy. Don’t worry. You can discover by yourself why you need one. The router sitting in your house has one installed in it. And please don’t disable that by any mean. You can check why a firewall is important […]

How to install OpenVAS on FreeBSD
Was ist das? OpenVAS is a vulnerability scanner. If you are unfamiliar to the vulnerability scanning world this can be an overwhelmingly experience but tools like this are what makes the matter more accessible, more manageable, easy to see and easy to fix. Before digging into the matter at hand here, that is how to […]

How to export a MySQL database.
You are your website editor, owner and now administrator. You want control over the whole process and you are migrating from a managed site. Or you are a versed user on unix-like environments and you are just willing to export your database. This is a simple post on how to export a MySQL database. If […]
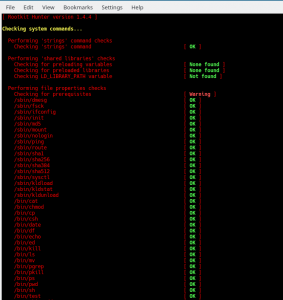
How to install RKHunter on FreeBSD
In this post you will find simple instructions to install rkhunter on FreeBSD which is a root kit “hunter” so your system/s will have some security in place for that kind of unwanted software. But for those who do not know what a rootkit is, let’s give it a simple definition (which you can get […]