
WARNING: A newer version of ModSecurity is available. The article to install ModSecurity 3 on FreeBSD can be found here. Will be published on March 1st, 2021.
If you find the articles in Adminbyaccident.com useful to you, please consider making a donation.
Use this link to get $200 credit at DigitalOcean and support Adminbyaccident.com costs.
Get $100 credit for free at Vultr using this link and support Adminbyaccident.com costs.
Mind Vultr supports FreeBSD on their VPS offer.
Before we get into the how to install ModSecurity 2 on FreeBSD 11 let’s address the first question. What is this thing and why is necessary? As I wrote a few weeks ago on a general security article ModSecurity is basically a web application firewall. As themselves explain this is a real-time application security monitoring and access control tool. It logs http(s) traffic in a continuous passive manner, allowing you to harden and secure your web application.
How does this go? Well, ModSecurity is an open source program that sets a platform to secure your web application with rules. You can write those rules, enable more things, or set it more open. But you can also get rules written by the OWASP (Open Web Application Security Project) community and if you wish you can also obtain rules from a commercial brand called Trustwave SpiderLabs.
There are two ways to get ModSecurity working on your system. One is putting it on a reverse proxy. I would recommend doing it this way in the case you need not only strict access but you are managing a significantly visited website or you may be even protecting several sites since you are giving protection services or even hosting them for profit. However you may be just pretending to protect your single web page or any other kind of web application you’re serving. This is where the so called embedded ModSecurity comes in. This is the way what you will find on this how to install ModSecurity on FreeBSD.
So let’s get into it:
First we’ll look for the package itself.
[Cabra@Sovietica ~]$ pkg search mod_security
ap24-mod_security-2.9.2_2 Intrusion detection and prevention engine
mod_security3-3.0.2 Intrusion detection and prevention engine
[Cabra@Sovietica ~]$
As you can see there are two relevant packages here. The standalone version and the Apache module. For this example we’ll use a freshly new created Apache install using one of my favourite features on FreeBSD which is Jails. To use that framework, which for the the newbies can be shortly explained as something similar to “Linux containers” but with all the security already in place, we’ll use iocage. You can follow this same steps if this is your first time and you just want to play with this before you get serious and go to pre-production or even straight to pro.
We first create the jail. The command is quite explanatory so I won’t comment here. Read the docs to get full info.
albert@BSDVM:~ % sudo iocage create --release=11.1-RELEASE --name=modsec ip4_addr="em0|192.168.1.202/24"
modsec successfully created!
albert@BSDVM:~ %
If it’s your first time using iocage you can skip this step, but for me I will have to update the just created jail since the image I am using to create this jail is a bit outdated.
albert@BSDVM:~ % sudo iocage update modsec
* Updating modsec to the latest patch level...
src component not installed, skipped
Looking up update.FreeBSD.org mirrors... 3 mirrors found.
Fetching metadata signature for 11.1-RELEASE from update5.freebsd.org... done.
Fetching metadata index... done.
Fetching 2 metadata patches.. done.
Applying metadata patches... done.
Inspecting system... done.
Preparing to download files... done.
Fetching 113 patches.....10....20....30....40....50....60....70....80....90....100....110. done.
Applying patches... done.
……
src component not installed, skipped
Installing updates... done.
modsec has been updated successfully.
albert@BSDVM:~ %
Let’s fire up the modsec jail, install apache and then straight to the matter: how to install modsecurity on FreeBSD.
albert@BSDVM:~ % sudo iocage start modsec
* Starting modsec
+ Started OK
+ Starting services OK
albert@BSDVM:~ %
We now get into it by typing:
albert@BSDVM:~ % sudo iocage console modsec
FreeBSD 11.1-RELEASE-p9 (GENERIC) #0: Tue Apr 3 16:59:16 UTC 2018
Welcome to FreeBSD!
………...
root@modsec:~ #
Once in, let’s bootstrap the package management tool on FreeBSD and install Apache.
root@modsec:~ # pkg search apache
The package management tool is not yet installed on your system.
Do you want to fetch and install it now? [y/N]: y
Bootstrapping pkg from pkg+http://pkg.FreeBSD.org/FreeBSD:11:amd64/quarterly, please wait...
Verifying signature with trusted certificate pkg.freebsd.org.2013102301... done
[modsec] Installing pkg-1.10.5...
[modsec] Extracting pkg-1.10.5: 100%
……….
unspeakable amount of packages listed based on the string “apache”
……….
and the ones you’re looking for:
apache22-2.2.34_4 Version 2.2.x of Apache web server with prefork MPM
apache24-2.4.33 Version 2.4.x of Apache web server
root@modsec:~ #
Let’s install the latest version:
root@modsec:~ # pkg install apache24
Updating FreeBSD repository catalogue...
FreeBSD repository is up to date.
All repositories are up to date.
Updating database digests format: 100%
The following 12 package(s) will be affected (of 0 checked):
New packages to be INSTALLED:
apache24: 2.4.33
libnghttp2: 1.31.1
libxml2: 2.9.7
expat: 2.2.5
perl5: 5.26.2
pcre: 8.40_1
apr: 1.6.3.1.6.1_1
gdbm: 1.13_1
indexinfo: 0.3.1
readline: 7.0.3_1
gettext-runtime: 0.19.8.1_1
db5: 5.3.28_6
Number of packages to be installed: 12
The process will require 145 MiB more space.
34 MiB to be downloaded.
Proceed with this action? [y/N]: y
…………….
[modsec] [12/12] Installing apache24-2.4.33...
===> Creating groups.
Using existing group 'www'.
===> Creating users
Using existing user 'www'.
[modsec] [12/12] Extracting apache24-2.4.33: 100%
……………..
root@modsec:~ #
Ok. Now let’s append the line that fires up Apache any time we boot the system to the correspondent file, since this is the FreeBSD way.
root@modsec:~ # sysrc apache24_enable="YES"
apache24_enable: -> YES
root@modsec:~ #
We now start the Apache webserver.
root@modsec:~ # service apache24 onestart
Performing sanity check on apache24 configuration:
AH00557: httpd: apr_sockaddr_info_get() failed for modsec
AH00558: httpd: Could not reliably determine the server's fully qualified domain name, using 127.0.0.1. Set the 'ServerName' directive globally to suppress this message
Syntax OK
Starting apache24.
AH00557: httpd: apr_sockaddr_info_get() failed for modsec
AH00558: httpd: Could not reliably determine the server's fully qualified domain name, using 127.0.0.1. Set the 'ServerName' directive globally to suppress this message
root@modsec:~ #
Don’t pay attention to the error message now, you will fix that later when configuring Apache to work with your application. For testing purposes this is just fine. Let’s check it’s actually working by going to our browser and point it to the ip address we’ve given to the jail. A message stating “It works!” has to appear before our eyes.
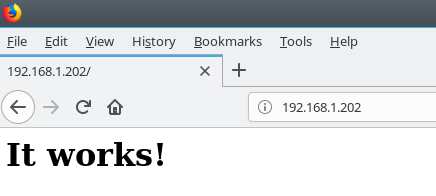
And indeed it does. Let’s now go for the main dish on this meal. Since we know the package name we’ll go for it straight.
root@modsec:~ # pkg install ap24-mod_security
Updating FreeBSD repository catalogue...
FreeBSD repository is up to date.
All repositories are up to date.
The following 4 package(s) will be affected (of 0 checked):
New packages to be INSTALLED:
ap24-mod_security: 2.9.2_2
curl: 7.59.0
ca_root_nss: 3.36.1
yajl: 2.1.0
Number of packages to be installed: 4
The process will require 7 MiB more space.
2 MiB to be downloaded.
Proceed with this action? [y/N]: y
[modsec] [1/4] Fetching ap24-mod_security-2.9.2_2.txz: 100% 247 KiB 252.8kB/s 00:01
[modsec] [2/4] Fetching curl-7.59.0.txz: 100% 1 MiB 1.2MB/s 00:01
[modsec] [3/4] Fetching ca_root_nss-3.36.1.txz: 100% 292 KiB 299.2kB/s 00:01
[modsec] [4/4] Fetching yajl-2.1.0.txz: 100% 55 KiB 56.8kB/s 00:01
Checking integrity... done (0 conflicting)
[modsec] [1/4] Installing ca_root_nss-3.36.1...
[modsec] [1/4] Extracting ca_root_nss-3.36.1: 100%
[modsec] [2/4] Installing curl-7.59.0...
[modsec] [2/4] Extracting curl-7.59.0: 100%
[modsec] [3/4] Installing yajl-2.1.0...
[modsec] [3/4] Extracting yajl-2.1.0: 100%
[modsec] [4/4] Installing ap24-mod_security-2.9.2_2...
[modsec] [4/4] Extracting ap24-mod_security-2.9.2_2: 100%
Message from ca_root_nss-3.36.1:
********************************* WARNING *********************************
FreeBSD does not, and can not warrant that the certification authorities
whose certificates are included in this package have in any way been
audited for trustworthiness or RFC 3647 compliance.
Assessment and verification of trust is the complete responsibility of the
system administrator.
*********************************** NOTE **********************************
This package installs symlinks to support root certificates discovery by
default for software that uses OpenSSL.
This enables SSL Certificate Verification by client software without manual
intervention.
If you prefer to do this manually, replace the following symlinks with
either an empty file or your site-local certificate bundle.
* /etc/ssl/cert.pem
* /usr/local/etc/ssl/cert.pem
* /usr/local/openssl/cert.pem
***************************************************************************
Message from ap24-mod_security-2.9.2_2:
You have installed ModSecurity.
To enable ModSecurity in Apache, follow the instructions in
/usr/local/etc/apache24/modules.d/280_mod_security.conf
Most users will use the signatures from the OWASP Core Rule Set (CRS).
For configuration instructions, see /usr/local/share/doc/mod_security2/README.
root@modsec:~ #
Pay attention to the install message. There is a recently created file called 280_mod_security.conf. Let’s see its content:
root@modsec:~ # cat /usr/local/etc/apache24/modules.d/280_mod_security.conf
## $FreeBSD: branches/2018Q2/www/mod_security/files/280_mod_security.conf.sample.in 413465 2016-04-16 17:29:07Z ohauer $
## vim: set filetype=apache:
##
## module file for mod_security
##
## PROVIDE: mod_security2
## REQUIRE: mod_unique_id
##
## To enable ModSecurity in Apache, enable the modules
## mod_unique_id (in httpd.conf) and
## mod_security2 in this config file
##
## Additionally, load configuration and rules with an Include line from
## /usr/local/etc/modsecurity/*.conf
##
## Most users will use the signatures from the OWASP Core Rule Set (CRS).
## For configuration instructions, see /usr/local/share/doc/mod_security2/README.
##
## apache modules for mod_security
#LoadModule unique_id_module libexec/apache24/mod_unique_id.so
#LoadModule security2_module libexec/apache24/mod_security2.so
#Include /usr/local/etc/modsecurity/*.conf
root@modsec:~ #
To enable the integration of ModSecurity into the Apache web server you just have to uncomment the last three lines and restart Apache so this newly created configuration file gets loaded. So this file should look like:
LoadModule unique_id_module libexec/apache24/mod_unique_id.so
LoadModule security2_module libexec/apache24/mod_security2.so
Include /usr/local/etc/modsecurity/*.conf
root@modsec:~ #
Before we reload Apache we will have to get the CRS rules. The mod_security’s Apache module is installed but it lacks rules. Let’s go for them.
We will first install git. Why? Well, there is a repository in git where the rules are regularly updated. You will grab them from there and from now on you will also regularly update your rules from that very repository.
root@modsec:~ # pkg install git
Updating FreeBSD repository catalogue...
FreeBSD repository is up to date.
All repositories are up to date.
The following 8 package(s) will be affected (of 0 checked):
New packages to be INSTALLED:
git: 2.16.3
p5-Authen-SASL: 2.16_1
p5-GSSAPI: 0.28_1
p5-Digest-HMAC: 1.03_1
python27: 2.7.14_1
libffi: 3.2.1_2
p5-Error: 0.17025
cvsps: 2.1_2
Number of packages to be installed: 8
The process will require 95 MiB more space.
15 MiB to be downloaded.
Proceed with this action? [y/N]: y
……………..
unspeakable amount of output
……………..
root@modsec:~ #
We now move to the modsecurity configuration directory. Do it since you will download the rules from git to just that place.
root@modsec:~ # cd /usr/local/etc/modsecurity
Let’s download the files:
root@modsec:/usr/local/etc/modsecurity # git clone https://github.com/SpiderLabs/owasp-modsecurity-crs
Cloning into 'owasp-modsecurity-crs'...
remote: Counting objects: 6773, done.
remote: Compressing objects: 100% (34/34), done.
remote: Total 6773 (delta 21), reused 11 (delta 5), pack-reused 6734
Receiving objects: 100% (6773/6773), 2.42 MiB | 747.00 KiB/s, done.
Resolving deltas: 100% (4793/4793), done.
root@modsec:/usr/local/etc/modsecurity #
The rules file is located in the newly created owasp-modsecurity-crs directory. Just take a look at the content in that directory.
root@modsec:/usr/local/etc/modsecurity # cd owasp-modsecurity-crs
root@modsec:/usr/local/etc/modsecurity/owasp-modsecurity-crs # ll
total 140
drwxr-xr-x 8 root wheel 13 May 6 19:56 .git/
-rw-r--r-- 1 root wheel 253 May 6 19:56 .gitignore
-rw-r--r-- 1 root wheel 362 May 6 19:56 .gitmodules
-rw-r--r-- 1 root wheel 229 May 6 19:56 .travis.yml
-rw-r--r-- 1 root wheel 45403 May 6 19:56 CHANGES
-rw-r--r-- 1 root wheel 192 May 6 19:56 CONTRIBUTORS
-rw-r--r-- 1 root wheel 460 May 6 19:56 IDNUMBERING
-rw-r--r-- 1 root wheel 16557 May 6 19:56 INSTALL
-rw-r--r-- 1 root wheel 2772 May 6 19:56 KNOWN_BUGS
-rw-r--r-- 1 root wheel 11357 May 6 19:56 LICENSE
-rw-r--r-- 1 root wheel 2344 May 6 19:56 README.md
-rw-r--r-- 1 root wheel 30221 May 6 19:56 crs-setup.conf.example
drwxr-xr-x 3 root wheel 4 May 6 19:56 documentation/
drwxr-xr-x 2 root wheel 5 May 6 19:56 id_renumbering/
drwxr-xr-x 2 root wheel 48 May 6 19:56 rules/
drwxr-xr-x 12 root wheel 16 May 6 19:56 util/
root@modsec:/usr/local/etc/modsecurity/owasp-modsecurity-crs #
This is now just to steps away to end. We will first put the crs-setup configuration file in place and we’ll then point the Apache’s configuration module file to the rules directory.
Look first for the crs-setup.conf.example file. Copy it as follows into the following path:
root@modsec:/usr/local/etc/modsecurity/owasp-modsecurity-crs # cp crs-setup.conf.example /usr/local/etc/modsecurity/crs-setup.conf
root@modsec:/usr/local/etc/modsecurity/owasp-modsecurity-crs #
Let’s tackle the final configuration step. We now edit the module’s file:
root@modsec:~ # vi /usr/local/etc/apache24/modules.d/280_mod_security.conf
And add the last line so it ends up looking as follows:
## apache modules for mod_security
LoadModule unique_id_module libexec/apache24/mod_unique_id.so
LoadModule security2_module libexec/apache24/mod_security2.so
Include /usr/local/etc/modsecurity/*.conf
Include /usr/local/etc/modsecurity/owasp-modsecurity-crs/rules/*.conf
Before restarting Apache to load the new configuration files and have everything working there is one change we need to apply at the modsecurity.conf file. If we look at the first 10 lines of the file we will find a sentence where we can read it is enabled but on “DectectionOnly” mode. We want to get it working full throttle.
root@modsec:/usr/local/etc/modsecurity # head -10 modsecurity.conf
# -- Rule engine initialization ----------------------------------------------
# Enable ModSecurity, attaching it to every transaction. Use detection
# only to start with, because that minimises the chances of post-installation
# disruption.
#
SecRuleEngine DetectionOnly
# -- Request body handling ---------------------------------------------------
root@modsec:/usr/local/etc/modsecurity #
So instead of “DetectionOnly” we will write the word “On”. It should look like:
root@modsec:/usr/local/etc/modsecurity # head -10 modsecurity.conf
# -- Rule engine initialization ----------------------------------------------
# Enable ModSecurity, attaching it to every transaction. Use detection
# only to start with, because that minimises the chances of post-installation
# disruption.
#
SecRuleEngine On
# -- Request body handling ---------------------------------------------------
root@modsec:/usr/local/etc/modsecurity #
We finally restart the Apache web server so the new modifications take effect and ModSecurity starts working with it.
root@modsec:~ # apachectl restart
Performing sanity check on apache24 configuration:
AH00557: httpd: apr_sockaddr_info_get() failed for modsec
AH00558: httpd: Could not reliably determine the server's fully qualified domain name, using 127.0.0.1. Set the 'ServerName' directive globally to suppress this message
Syntax OK
Stopping apache24.
Waiting for PIDS: 8814.
Performing sanity check on apache24 configuration:
AH00557: httpd: apr_sockaddr_info_get() failed for modsec
AH00558: httpd: Could not reliably determine the server's fully qualified domain name, using 127.0.0.1. Set the 'ServerName' directive globally to suppress this message
Syntax OK
Starting apache24.
AH00557: httpd: apr_sockaddr_info_get() failed for modsec
AH00558: httpd: Could not reliably determine the server's fully qualified domain name, using 127.0.0.1. Set the 'ServerName' directive globally to suppress this message
root@modsec:~ #
This is all on the how to install modsecurity on FreeBSD. I will create a new article or may update this very one for a standalone installation but it’s still unplanned. If you want more information go to the project’s wiki at github and drink whatever you may need.
If you find the articles in Adminbyaccident.com useful to you, please consider making a donation.
Use this link to get $200 credit at DigitalOcean and support Adminbyaccident.com costs.
Get $100 credit for free at Vultr using this link and support Adminbyaccident.com costs.
Mind Vultr supports FreeBSD on their VPS offer.