
Update 05-2020: If anyone is interested on the automatic process you can read my tutorial on DigitalOcean about the topic.
On this guide we will manually update our Letsencrypt certificate on FreeBSD for a single website. It is a simple operation that can be automated as a cron job, but seeing it is always informative and educative.
If you find the articles in Adminbyaccident.com useful to you, please consider making a donation.
Use this link to get $200 credit at DigitalOcean and support Adminbyaccident.com costs.
Get $100 credit for free at Vultr using this link and support Adminbyaccident.com costs.
Mind Vultr supports FreeBSD on their VPS offer.
To get a general idea about certificates do not hesitate to click on this link.
The system’s name and username have been changed so you won’t know what I am playing with. You don’t need to know those bits. I hope you get my sense of humor though.
Soviet@Union:~ % uname -a
FreeBSD Collector 11.0-RELEASE-p15 FreeBSD 11.0-RELEASE-p15 #0: Tue Nov 14 08:04:40 UTC 2017 [email protected]:/usr/obj/usr/src/sys/GENERIC amd64
Soviet@Union:~ %
The first thing is stopping the Apache web server.
Soviet@Union:~ % sudo service apache24 status
apache24 is running as pid 828.
Soviet@Union:~ % sudo service apache24 stop
Stopping apache24.
Waiting for PIDS: 828.
Soviet@Union:~ %
We now put the command to renew the letsencrypt certificate.
Soviet@Union:~ % sudo certbot certonly
Saving debug log to /var/log/letsencrypt/letsencrypt.log
How would you like to authenticate with the ACME CA?
-------------------------------------------------------------------------------
1: Spin up a temporary webserver (standalone)
2: Place files in webroot directory (webroot)
-------------------------------------------------------------------------------
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 1
Plugins selected: Authenticator standalone, Installer None
Please enter in your domain name(s) (comma and/or space separated) (Enter 'c' to cancel): www.adminbyaccident.com adminbyaccident.com
-------------------------------------------------------------------------------
You have an existing certificate that contains a portion of the domains you requested (ref:
/usr/local/etc/letsencrypt/renewal/adminbyaccident.com-0001.conf)
It contains these names: adminbyaccident.com
You requested these names for the new certificate: www.adminbyaccident.com, adminbyaccident.com.
Do you want to expand and replace this existing certificate with the new certificate?
-------------------------------------------------------------------------------
(E)xpand/(C)ancel: E
Renewing an existing certificate
Performing the following challenges:
tls-sni-01 challenge for www.adminbyaccident.com
tls-sni-01 challenge for adminbyaccident.com
Waiting for verification...
Cleaning up challenges
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/usr/local/etc/letsencrypt/live/adminbyaccident.com-0001/fullchain.pem
Your key file has been saved at:
/usr/local/etc/letsencrypt/live/adminbyaccident.com-0001/privkey.pem
Your cert will expire on 2018-04-21. To obtain a new or tweaked version of this certificate in the future, simply run certbot again. To non-interactively renew *all* of your certificates, run "certbot renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
Soviet@Union:~ %
After this we will find our certificates on the path the notes say. We will only have to place them on the path we set on our Apache configuration. In this case the website configuration is found on a manually created path.
/usr/local/etc/apache24/ssl/letsencrypt
There are two files on that path wich are the key and the certificate from the previous period. As you may know letsencrypt certificates last for three months. We will rename them first, copy the new certificate into the path, start the Apache web server and then remove the old certificates.
Soviet@Union:/usr/local/etc/apache24/ssl/letsencrypt/adminbyaccident.com % ll
total 11
-rw-r--r-- 1 root wheel 1818 22 oct. 12:05 cert.pem
-rw-r--r-- 1 root wheel 1708 22 oct. 12:05 privkey.pem
Soviet@Union:/usr/local/etc/apache24/ssl/letsencrypt/adminbyaccident.com %
We now rename the old files:
Soviet@Union:/usr/local/etc/apache24/ssl/letsencrypt/adminbyaccident.com % sudo mv cert.pem cert.pem.old
Soviet@Union:/usr/local/etc/apache24/ssl/letsencrypt/adminbyaccident.com % sudo mv privkey.pem privkey.pem.old
We copy as root the new files to the right path:
root@Union:/usr/local/etc/letsencrypt/live/adminbyaccident.com-0001 # cp cert.pem /usr/local/etc/apache24/ssl/letsencrypt/adminbyaccident.com/
root@Union:/usr/local/etc/letsencrypt/live/adminbyaccident.com-0001 # cp privkey.pem /usr/local/etc/apache24/ssl/letsencrypt/adminbyaccident.com
Once the two files have been copied to the right location we will check Apache’s configuration and if it’s ok we will start it up.
root@Union:/usr/local/etc/letsencrypt/live/adminbyaccident.com-0001 # apachectl configtest
Performing sanity check on apache24 configuration:
Syntax OK
root@Union:/usr/local/etc/letsencrypt/live/adminbyaccident.com-0001 # apachectl start
Performing sanity check on apache24 configuration:
Syntax OK
Starting apache24.
Everything should be working.
Soviet@Union:~ % sudo apachectl status
apache24 is running as pid 88318.
Soviet@Union:~ %
And indeed it is but the clearest way to see our letsencrypt certificate is being serverd is going to the browser.
So green has always been identified as ok. Let’s now check the certificate and what it says.
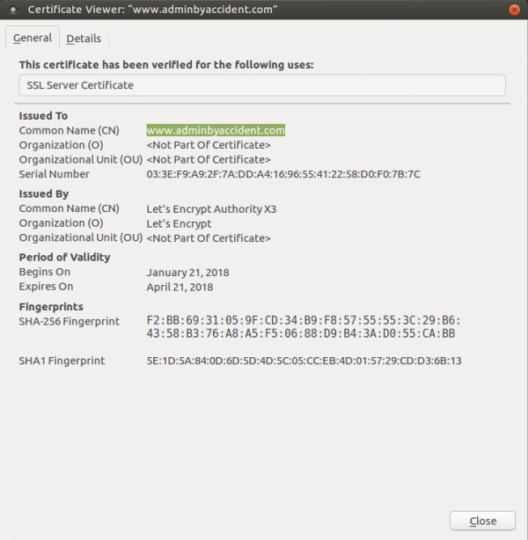
And here it is. Here we have our just recently created certificate, validated and issued by letsencrypt.
We need to be quick since using this method we’ve stopped our web server and the page is not running. There is an alternative method, using the webroot option where you don’t need to stop the webserver.
That would work by issuing the following command:
sudo certbot certonly --webroot -w /path/to/the/site -d domain.com -d www.domain.com
This will create the certificate, key, fullchain, etc in the same directory as in the method shown before.
Again, you will have to copy the certificate an the key to the path you set in your Apache configuration.
More official information about the install and use can be found at this address.
https://certbot.eff.org/all-instructions
For automatic LetsEncrypt setup on FreeBSD read my tutorial at DigitalOcean.
If you find the articles in Adminbyaccident.com useful to you, please consider making a donation.
Use this link to get $200 credit at DigitalOcean and support Adminbyaccident.com costs.
Get $100 credit for free at Vultr using this link and support Adminbyaccident.com costs.
Mind Vultr supports FreeBSD on their VPS offer.