Millions of emails are sent and received every day. Most of them are just junk. And many among those are potentially harmful. Phishing still is one of the most effective ways for malicious actors to penetrate into well secured networks. The weakest link, too often, is the human factor. Training can help mitigate this 24×7 all year-round risk and spam filtering has got cleverer through time. However there are times when suspicious email gets into workstations despite all our best efforts. Some software incorporates easy to use add-ons so users can label a piece of mail and that is automatically reported to the security team at the company or service provider. Once that is done, what can a system administrator or a security analyst do?
If you find the articles in Adminbyaccident.com useful to you, please consider making a donation.
Use this link to get $200 credit at DigitalOcean and support Adminbyaccident.com costs.
Get $100 credit for free at Vultr using this link and support Adminbyaccident.com costs.
Mind Vultr supports FreeBSD on their VPS offer.
Collect information
Gathering information from that email is vital to discern from just crap that doesn’t represent a thread from the really worrying stuff. This is the very first step into how to analyze suspicious email.
First we have to collect all the links appearing on that email. And be very wary of clicking on them. Do it on a VM and be very careful anyways, your network may not be very secure and be wide open, something bad actors love.
Once all links have been collected there are paid tools to use but there are other free ones to choose from, such as virustotal. A very well reputed service from a chap from Málaga who created this company now owned by Google. Once we insert a suspicious URL on that box an analysis will begin. Viruses will be looked for with the assistance of dozens of antivirus software, links to other domains or URLs will be followed, etc, etc.
We all receive lots of email, specially spam and I have selected this one entitled ‘Bitcoind code’ from a very dubious sender. The text in it tries to convince me to get some software and earn money by running it on my device. Hell no!
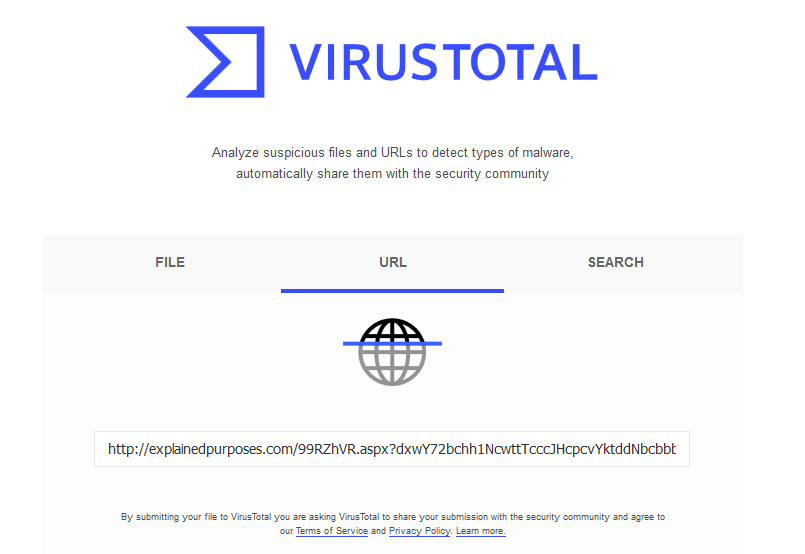
As depicted in the image above the link can be inserted in the box and be analyed. This is the result.
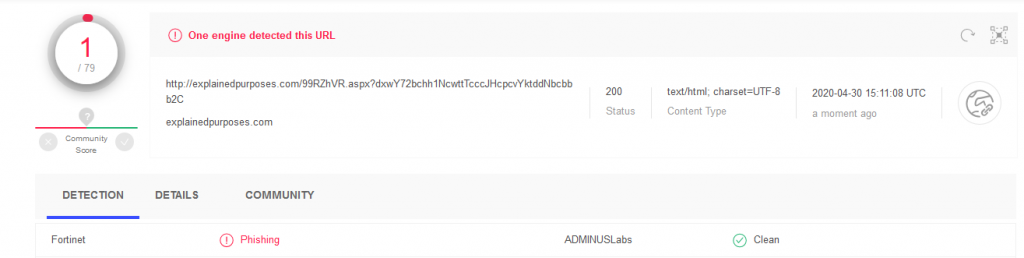
Unfortunately just one antivirus engine got this is a malicious phishing URL. This happens all the time and engines need feedback from users, analysts and security companies to keep the pace and block all this every day malicious activity.
If we further check into the ‘Details’ tab we can get more information, quite often very useful.
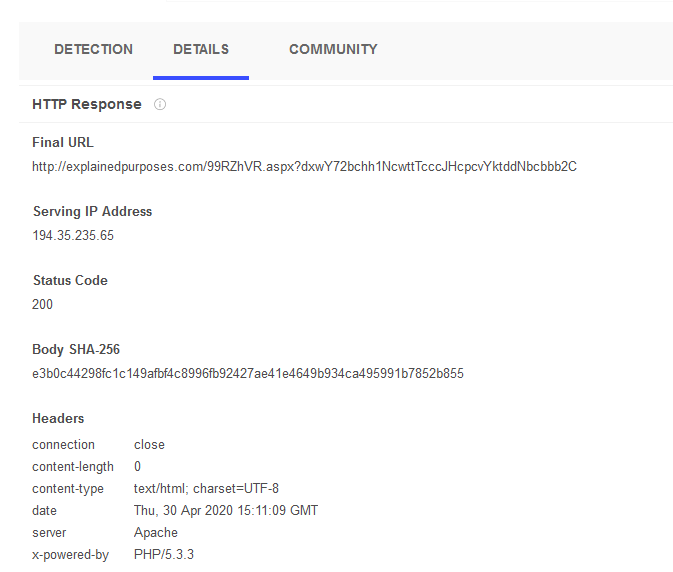
This time there are no redirects, however we can see an IP address. Write that down, next to the URLs you are analysing. If redirects are present it is wise to also collect those intermediate URLs, the domains associated to those and all of the IPs as well.
We can make use of another free tool to check the reputation of an IP. The Cisco Talos Intelligence Group is a security group put in place by Cisco. And they have a very interesting free service to make some checks.
If I check the IP revealed by virustotal:
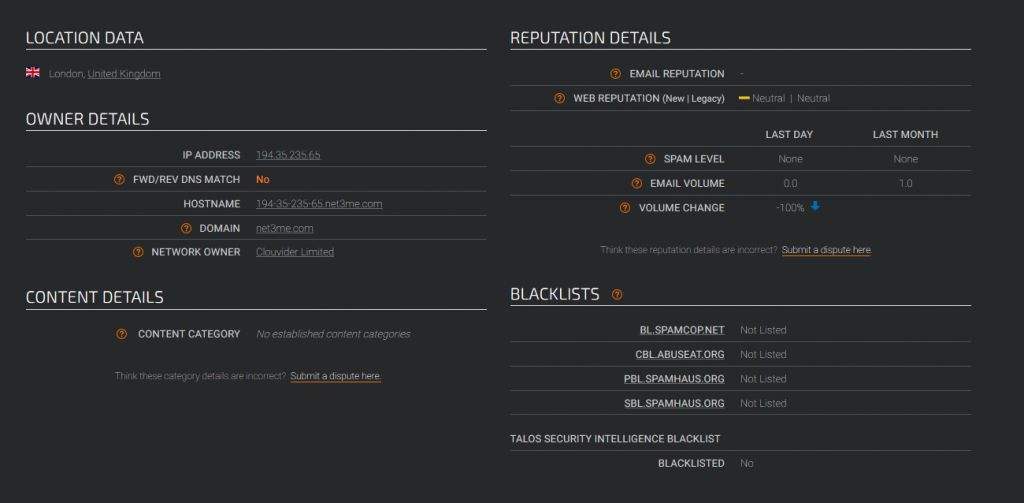
A fairly clean IP. Quite often IPs related to spam or other nefarious activity appear with ‘poor’ scores and they have also been reported in the past. Such reports doesn’t seem to apply to this IP.
The sent email history report does also indicate this was used for just one day. Attackers or just fraudsters are often sneaky and move quickly.
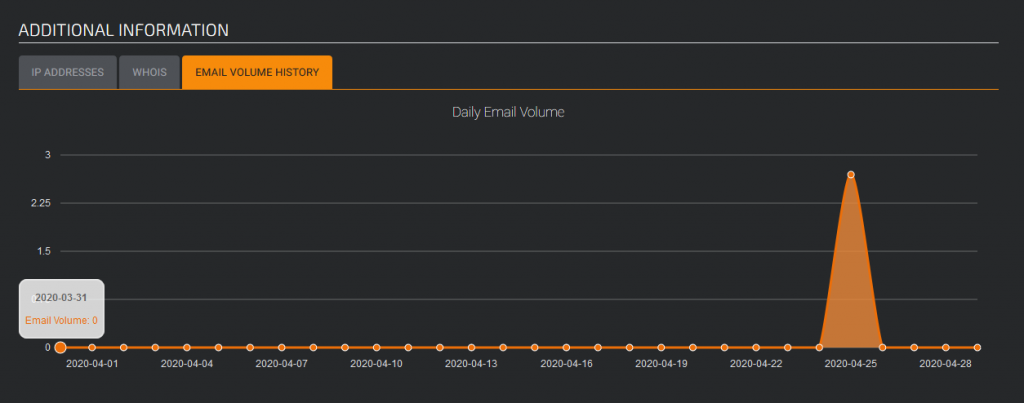
So far, with these tools, we have collected URLs, domain names and IPs. But there’s still more to do. We can look at the email headers.
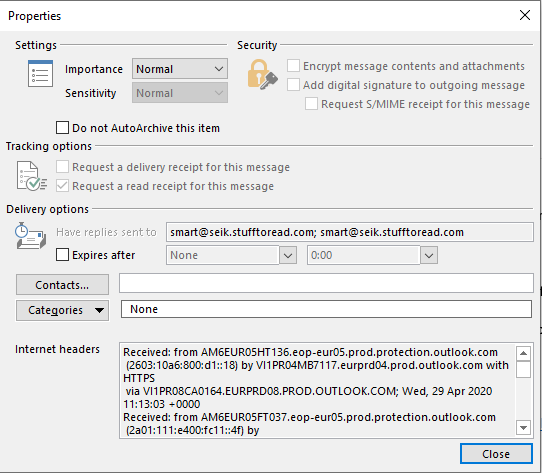
Depending on the client we are using the method to obtain the headers will vary. This is what we need to see if we are using Microsoft’s Outlook heavy client (not the web version).

This on the right are the headers. We can make use of a header analyzer to spot domains the links in the body did not include. Google has a free of charge header analyzer. But you can make use of other free tools such as the one from MXToolBox. All we need to do is copy all the headers content and paste it to analyze it.
In this case the headers reveal this:
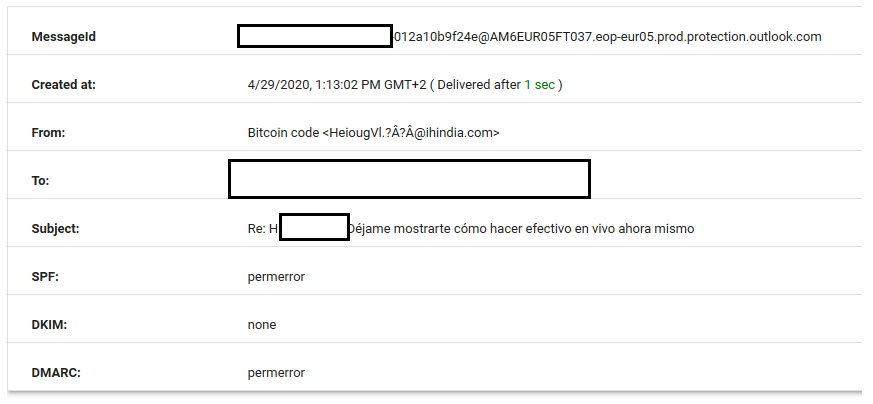
There are some email protection mechanisms such as SPF, DKIM and DMARC that show errors or no availability. Luckily Outlook did already send this mail to the Junk inbox for me. Probably because of the links and the suspicious content as well as the origin address.
Some times the header will reveal the email has bounced across several servers and domains. Collect those domains too, since this information will be of utility later.
Last, but not least, we need to check for any payload attached to the email. Maybe the antivirus software has removed some type of attachment found in the original mail. Grab a sample whenever you can, and obviously don’t execute it and be very careful when opening files. It’s much safer to do these things inside VMs to minimize the risk of infection. In the ‘analyze the impact section’ I mention a couple of free tools to help in analyzing attachments. Don’t discard virustotal, it can help here too.
Block the sender on the email server
In the previous section we have collected information on the email. Of special interest are the domains. Check them first before blocking any. For example an domain could be from a service provider or a client and although they may have been spoofed we can’t block all of their emails since most of them would be legitimate. If we did so we could cause trouble at our organization. But how can we check that?
Whois is a very nice UNIX/Linux tool, available in Windows systems either using the Windows Subsystem for Linux, or using Cygwin. Maybe you are running some virtualization software such as VMWare Workstation Player or VirtualBox with some VM inside. For those without such a toolset there are websites which provide this information and are funded by advertisements.
In this case we have an obvious domain, the one that sent the email but we could have several from the headers as well.
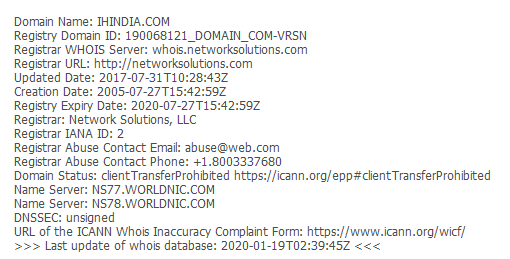
It is a registered domain and if, for example, the content would have had a malicious payload we could report this to the registrar abuse contact.
Of course we’d need to check with the allegedly recipient if a client or service provider holding that domain name exists in the company. Maybe we have access to a DB where shuch information is held. If the domain isn’t from a legitimate contact we can put this domain on a blocking list, either permanent or temporary. This list will be placed on our mail server.
Once we have filtered all the domain names and we have collected those malicious or undesired ones we can proceed to block them on our email server. However we need to take in consideration mail can be spoofed. This fact meaning companies can send correu electrònic they never intended to, nor they were aware of.
For example many companies do still run their mail servers without DKIM or DMARC, yet some do even have a very ‘libertarian’ SPF configuration with the ‘+all’ option enabled. Some of those companies or organizations may have legitimate contact with ours. Deal with it. For example just blocking the offensive address and not the whole domain, while warning them of such incident. Put a deadline for them to make the necessary corrections if this is repeated through time and the risk is increasing.
Don’t forget to analyze all the domains from the URLs and their redirects if any.
Blocking specific IPs is an option, however this should be only done temporarily. The reason being the relation between IPs and domains can quickly change. IPs do also go into a ‘cleaning’ process after they have been used. Some time in the past an IP could have been related to malicious activity but at a later time it may have been cleared and ready to use with a legitimate purpose. Who remembers about an IP blocked three years later? Nobody! More effective to block domains.
Analyze the impact
How many people has received that very email is crucial. It’s not the same an email received by 5 random people at the company than hundreds of recipients. Plus it’s not the same if those 5 are top people in the organization either.
First make use of the tools available on your mail setup to obtain such a vital information. But do also check who are some of the recipients in your organization with the tools available to you such as Active Directory or LPAdmin or Apache Directory Studio. The last two very suitable for OpenLDAP setups. If only 5 people received this suspicious email it could be just a false positive, but also it could be a targeted attack to very specific personnel up above in the organization. Mind users, almost everyone has some social network account like Facebook, Instagram but professional ones too like LinkedIn where relevant information is displayed.
Related to the next section it is always necessary to know if anyone has fallen into the trap and quite often that is clicking on a link or even introducing credentials on a spoofed website. There are sites appearing as legitimate ones such as logins for Microsoft’s services but in fact they aren’t. Users are just clunky sometimes and do not check domains in URLs, nor look for TLS connections or certificates. So they click on things they really shouldn’t. Security proxy software can help on identifying which users have clicked. Other types of software such as SIEM can be helpful. All we need is to check who has gone to a specific IP (the one the domain resolves to). If we haven’t got such a tool set, just looking (and filtering) the logs on the firewall can help.
Payloads. We also need to check them and evaluate the type of harm they can cause. In the first section it’s been advised to collect any kind of attachment or payload associated with the original message. Some security software such as malware analysis sandbox tools can be really helpful. This is one free tool called Cukoo and this other one which I’d recommend is called any.run. Both are free. The principle is anyone can run any suspicious binary inside those sandbox services, they are analyzed, and wait for the result. Depending on it, you will know what type of payload has been introduced and the general idea of what it does. From bitconin mining software draining power from workstations and servers alike to ransomware, through keyloggers and similar information extraction tools come in attachments. Acquiring this knowledge will help in determining impact and actions.
Once we have gathered information relative to the impact we can start making a draw of what happened and if any further action is needed on a very small scale or a large one.
Other blocking tools
Working at a large environment surely includes some type of proxy filtering for web browsing. Security software companies make different offerings on such products. IT or security staff can block certain categories or specific URLs so users can’t visit certain types of sites. Watching pr0n is usually forbidden at work (except if you work at such places where the content is produced, and no, pr0n is not a typo). But consuming video content can have an impact on bandwidth, which is sometimes not just expensive but scarce.
In the first step we didn’t collect links on the email just to obtain domains to analyze or check what risk those posed. We also did collect them to block users visiting them if they resulted to be harmful. Of course we’d need some kind of proxy browsing tool in place, otherwise the users do enjoy of fully-free browsing and that leaves them unprotected.
If for example an executable was attached we can check its signature and add that to our antivirus software as an object to block, so any machine in our environment is aware of this malicious binary. That obviously depends on our antivirus solution. Also note file extensions can be spoofed, so a file that looks like a picture may well be a spoofed file containing an executable.
Warn users
Not a simple task to do when many are affected. In a large environment warning users may be even need the assistance of the helpdesk team. Simple instructions, not too many details and an assertive message are key pieces to correctly and safely warn users about a thread in their inbox. Even if the attachment has a very malicious binary that can cause lots of harm to the company it’s better not to cause unnecessary alarm.
In smaller environments or cases where very few people are affected it’s much simpler to give them a call, or contacting them through skype. An email about an email may be useful but may cause confusion and a torrent of unnecessary warnings to the security team about this second piece. You know your people and yes, some are nuts. They are good at what they are and that doesn’t necessarily implies handling a computing device. How many of you admins or programmers do still fight with spreadsheets? Welcome.
But what to warn them about? This is a simple bullet point list.
– There’s a potentially harmful mail on the inbox.
– The title is: xxx. The sender is: xxx
– Find it. And do not open it.
– Delete it.
– In case it was previosly spotted and nothing was done, just delete it.
– If it was spotted and opened please report username.
– If any link was clicked please report username.
– If any credentials were entered anywhere please report username.
– If in doubt please contact the helpdesk service.
– If the computer is blocked or behaving strangely turn it off and report the case to the helpdesk service.
Combine the concepts above, and yours, to suit your needs.
Further actions
For those who have fallen into the trap, for example introducing credentials on a non-legitimate site the quickest and safest action is to change their domain password. But that is only one type of attack where the malicious actor just wanted to steal a username and a password.
Furthermore attackers may have not done a credential stealing attempt but a more nefarious and insidious type of attack such as planting a backdoor. In those cases an active, probably on-site intervention would be needed. Disconnecting the device from the network, scanning with several antivirus and antimalware tools will be necessary. The recent activity of such device with the help of IDS systems such as Suricata or SIEM software. If days later the same user and device are detected causing suspicious activity a complete reinstall of the operating system and software may be needed.
Final thoughts
Not clicking on every single link is a lesson we all have had to learn at some point. That doesn’t mean well trained personnel can’t be tricked. All of us can fall into one of those traps. Be aware of how similar does ‘.com’ look to ‘.corn’. Rub your eyes, I can wait. See? That simple. Luckily for us ‘.corn’ isn’t available as a top level domain. But there’s a good chance some similar domain to the one your company is using is free and some malicious actor tries to trick your staff.
Email security is hard. Filters have improved a lot and there are many tools available, from antivirus software to antispam. But now and then one of those unwanted mails sneak into the inbox. And boy they can cause harm in any environment.
Security shouldn’t rely on one or two aspects but an holistic approach should be taken. There are many steps to take and the bigger the environment is the bigger the challenge. I just hope this article has help a few admins and users.
If you find the articles in Adminbyaccident.com useful to you, please consider making a donation.
Use this link to get $200 credit at DigitalOcean and support Adminbyaccident.com costs.
Get $100 credit for free at Vultr using this link and support Adminbyaccident.com costs.
Mind Vultr supports FreeBSD on their VPS offer.