
Nessus is a very well known vulnerability scanner used by many large and small companies to assess their systems and correct the issues found in them. Cybersecurity teams and specially auditors, make heavy use of tools like this in order to follow up the state of infrastructure and environments. Having a tool like this saves lots of investigation time, crafting special scripts to gather information, and it gives the user the capacity to get reports in CSV and html formats. More on this on a later article.
Nessus isn’t the only tool available for this job. As mentioned before one can extract good information about vulnerabilities combining both a shell script, to extract information from a domain controller like Microsoft’s active directory, and a decent knowledge and extract of Microsoft’s Patch Tuesday like I’ve written for April 2020. Cross the information on both and you can elaborate your own report and procedures. However this job can be quite tedius, time consuming and it may give you errors.
If you find the articles in Adminbyaccident.com useful to you, please consider making a donation.
Use this link to get $200 credit at DigitalOcean and support Adminbyaccident.com costs.
Get $100 credit for free at Vultr using this link and support Adminbyaccident.com costs.
Mind Vultr supports FreeBSD on their VPS offer.
There are alternatives like IBM’s VMS, again IBM’s QRadar, or the fantastic open source tool OpenVAS which I wrote about a few months ago. One can even get decent information about vulnerabilities in a box or in an environment using Nmap or its graphical front end Zenmap but these two require good knowledge and are time consuming. Their advantage is a more than decent accuracy and they are cheap, as much as it can get, since they are free. Free of charge and they are free software too. Don’t get wrong here, security auditors love these tools and make good and even heavy use of them in some cases. But typically for smaller scopes than the other ones. I may even go as long as to say it’s not a matter of quality but scale and ease of use to extract information quickly.
Every single of these tools can get quite complicated (as almost anything in tech) and managing them, extracting all their juice, takes not just time time but a stable company willing to invest time, money and trust on their teams too. I’ve professionally used IBM VMS scanner (although QRadar as well but not for vulns), OpenVAS and Nessus. Each has its upsides and downsides. IBM’s VMS interface may result a bit clunky at times but it’s simple once you have been familiarized with it. Nessus is a bit more intuitive to use but both have the same type of tooling and options for the basic and more day to day use. I’d say though, Nessus’ advantage over IBM VMS would be the solution proposals are a bit clearer to see, as well as a bit more intuitive UI. But that’s it, both do the job quite similarly. OpenVAS is very intuitive to use, has good reporting and can be installed on every Kali Linux system very easily, something pentesters love.
Nessus has a so called ‘Community Edition’ that can be used free of charge for up to 16 boxes. And yes, it is a stripped down version from the ‘Professional’ one. You need to set up an account using your email address and you get a free license. This is enough for testing purposes without having to spend the beyond three thousand euros per year the full-fledged tool costs. However if you are short in budget OpenVAS is a no brainer. And even if you have it I’d consider it as a top choice next to Nessus.
I’ve set a CentOS 8 box and installed Nessus on a VM for testing. The installation process is dead simple. Get the free license at their website by selecing Nessus Essentials, download it and then install it on a CentOS VM using the following command:
# rpm -ivh Nessus-<version number>-es6.x86_64.rpm
Then run the daemon with this other one:
# service nessusd start
If you are using systemd, like I am. Just change it to:
# systemctl start nessusd.service
Yes, a very simple, quick and easy installation process. Then you’ll have to use the tool through your browser and typically using the default port 8834.
As you can see, there is a menu on the left and one of the first things you want to do is visiting the ‘Policies’ section.
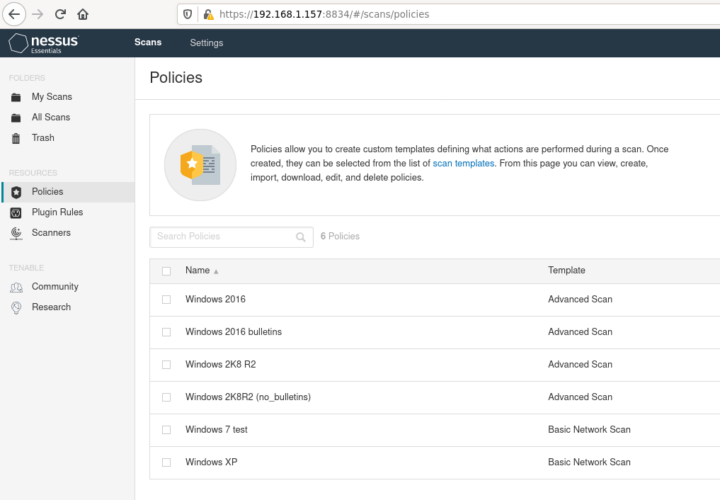
You will find this empty and in here you can choose what type of scan you wish to perform.

As you can see above there are already pre-defined templates you can make use of but be aware there are a few of them that are marked as ‘Upgrade’ ones, since they are not available without paid services.
Alternatively you can also choose to make and ‘Advanced Scan’ and choose from a few options by selecting the plugins you want to include. These contain relevant information for specific operating systems, other types of software or services.
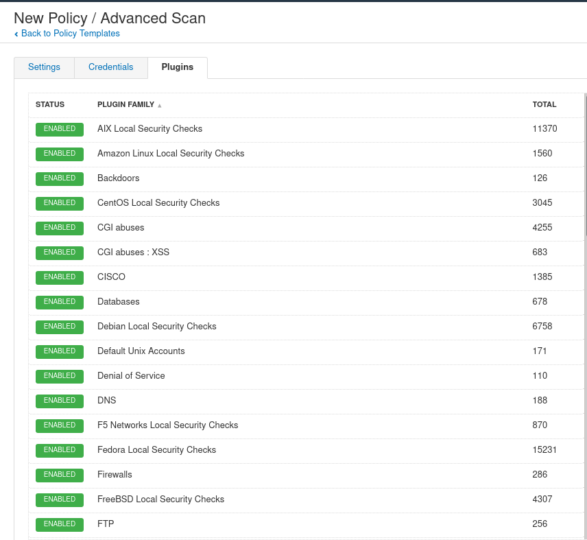
For example I wanted to scan a few Windows boxes in my lab environment. So I have chosen to build a policy using the specific plugins for Windows.
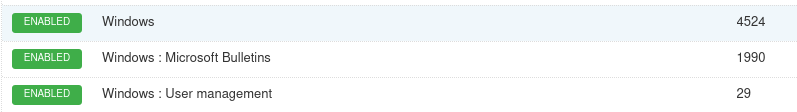
At the end you can set up a series of different scan templates manually so you can choose what type of scan you want to do.
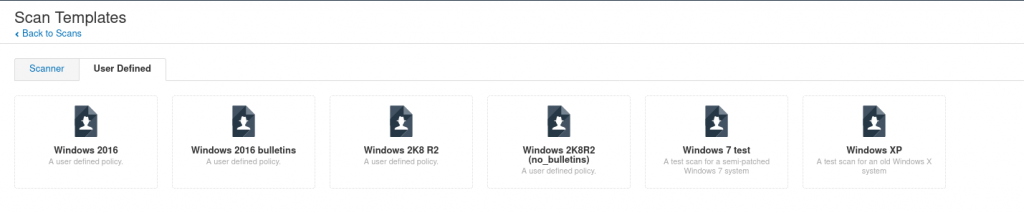
You only see Windows templates here since this is the activity I’ve given this tool. But I’ll be doing some other types of tests, for example on FreeBSD boxes or Linux ones, since Nessus incorporates dedicated plugins as well.
As we can see here below, preparing and launching (scheduled or manual) a new scan is quite easy.
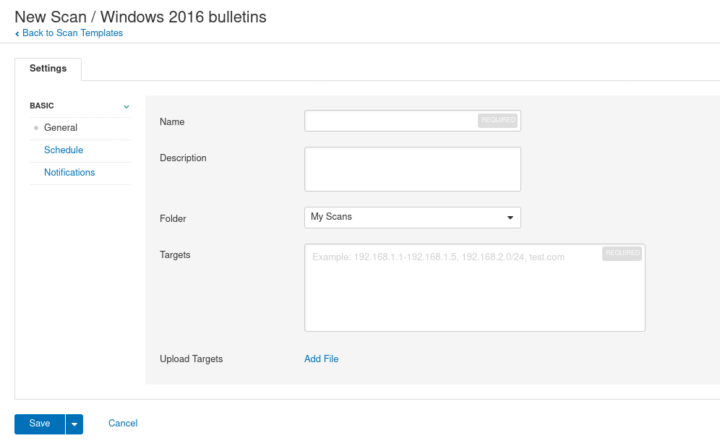
We have to select a policy, in this case above a Windows 2016 bulletins check only. You set the name of the scan, a short description if you need it, the place you want it to go, and the targets. On a paid subscription this can be larger than 16. Of course you’d better have the credentials already set on the policy, using a predefined local user, or better yet an Active Directory one, just used for this type of tasks.
This is all for this introduction to the Nessus vulnerability scanner.
If you find the articles in Adminbyaccident.com useful to you, please consider making a donation.
Use this link to get $200 credit at DigitalOcean and support Adminbyaccident.com costs.
Get $100 credit for free at Vultr using this link and support Adminbyaccident.com costs.
Mind Vultr supports FreeBSD on their VPS offer.