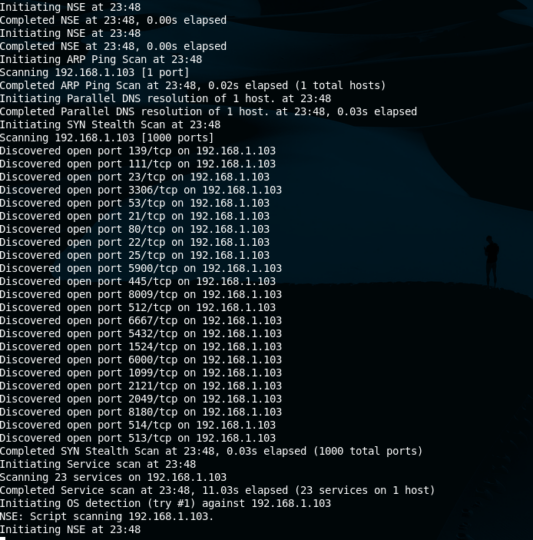
Nmap is a discovery tool used in security circles but very useful for network administrators or sysadmins. One can get information about operating systems, open ports, running apps with quite good accuracy. It can even be used in substitution to vulnerability scanners such as Nessus or OpenVAS for not very large environments, or quick audits.
If you find the articles in Adminbyaccident.com useful to you, please consider making a donation.
Use this link to get $200 credit at DigitalOcean and support Adminbyaccident.com costs.
Get $100 credit for free at Vultr using this link and support Adminbyaccident.com costs.
Mind Vultr supports FreeBSD on their VPS offer.
This is not a long explanatory article. Just a quick and dirty cheat sheet. This same flags can be found on Zenmap.
| nmap -sn | Ping scan | |
| nmap -T4 -F | Quick scan | |
| nmap -sV -T4 -O -F –version-light | Quick scan plus | |
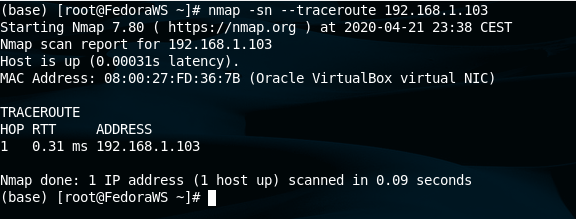
| nmap -sn –traceroute | Quick traceroute | |
| nmap | Regular scan | |
| nmap -T4 -A -v | Intense scan | |
| nmap -sS -sU -T4 -A -v | Intense scan plus UDP | |
| nmap -p 1-65535 -T4 -A -v | Intense scan, all TCP ports | |
| nmap -T4 -A -v -Pn | Intense scan, no ping |
Some captures of the shortests scans. Intense scans are basically quite long, check lots of things and even trigger some alert systems in some environments. Don’t use this tool indiscriminately, be wise.
If you find the articles in Adminbyaccident.com useful to you, please consider making a donation.
Disclaimer: The activity described here is just for demonstration purposes. I shall not be liable for any malicious use of the tools and processes here described. Attacking people, companies, devices, public or private technological property, without the permission of such entities, may constitute an offence punishable in your region/country, and such activities are strongly discouraged by the author.
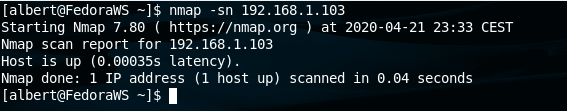
A ping scan output may look like this:
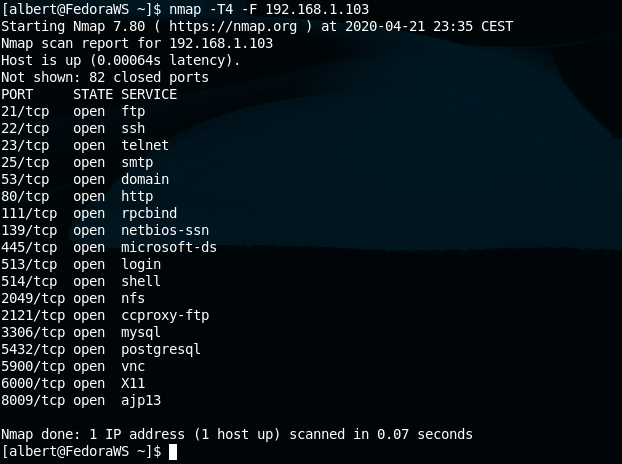
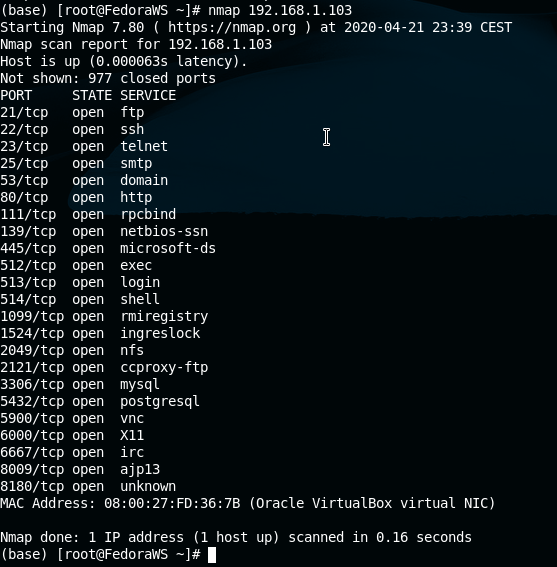
A quick scan may reveal more useful information, such as open ports on the target system.
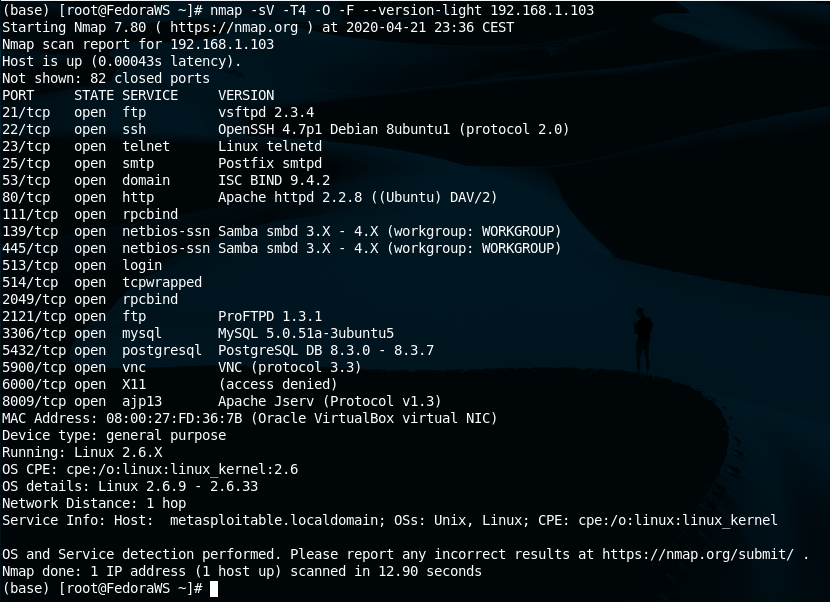
A quick scan plus will be useful for an auditor, since the versions of the running programs on the open ports will be displayed.
A quick traceroute scan will get you little information but useful one such as the MAC address on the target.
A regular scan will be… regular? Just kiddin’
The intense scan types reveal lots of information. Lots of it. But they do also stress things out quite a bit so be aware this can trigger warnings on security systems put in place to detect suspicious activity.
This is the text output of such type of scan in its simplest form:
(base) [root@FedoraWS ~]# nmap -T4 -A -v 192.168.1.103
Starting Nmap 7.80 ( https://nmap.org ) at 2020-04-21 23:40 CEST
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 23:40
Completed NSE at 23:40, 0.00s elapsed
Initiating NSE at 23:40
Completed NSE at 23:40, 0.00s elapsed
Initiating NSE at 23:40
Completed NSE at 23:40, 0.00s elapsed
Initiating ARP Ping Scan at 23:40
Scanning 192.168.1.103 [1 port]
Completed ARP Ping Scan at 23:40, 0.01s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 23:40
Completed Parallel DNS resolution of 1 host. at 23:40, 0.03s elapsed
Initiating SYN Stealth Scan at 23:40
Scanning 192.168.1.103 [1000 ports]
Discovered open port 80/tcp on 192.168.1.103
Discovered open port 139/tcp on 192.168.1.103
Discovered open port 111/tcp on 192.168.1.103
Discovered open port 5900/tcp on 192.168.1.103
Discovered open port 22/tcp on 192.168.1.103
Discovered open port 53/tcp on 192.168.1.103
Discovered open port 445/tcp on 192.168.1.103
Discovered open port 21/tcp on 192.168.1.103
Discovered open port 25/tcp on 192.168.1.103
Discovered open port 23/tcp on 192.168.1.103
Discovered open port 3306/tcp on 192.168.1.103
Discovered open port 1099/tcp on 192.168.1.103
Discovered open port 2049/tcp on 192.168.1.103
Discovered open port 513/tcp on 192.168.1.103
Discovered open port 1524/tcp on 192.168.1.103
Discovered open port 8180/tcp on 192.168.1.103
Discovered open port 8009/tcp on 192.168.1.103
Discovered open port 514/tcp on 192.168.1.103
Discovered open port 2121/tcp on 192.168.1.103
Discovered open port 512/tcp on 192.168.1.103
Discovered open port 5432/tcp on 192.168.1.103
Discovered open port 6000/tcp on 192.168.1.103
Discovered open port 6667/tcp on 192.168.1.103
Completed SYN Stealth Scan at 23:40, 0.03s elapsed (1000 total ports)
Initiating Service scan at 23:40
Scanning 23 services on 192.168.1.103
Completed Service scan at 23:41, 11.10s elapsed (23 services on 1 host)
Initiating OS detection (try #1) against 192.168.1.103
NSE: Script scanning 192.168.1.103.
Initiating NSE at 23:41
NSE: [ftp-bounce] PORT response: 500 Illegal PORT command.
Completed NSE at 23:41, 8.50s elapsed
Initiating NSE at 23:41
Completed NSE at 23:41, 0.09s elapsed
Initiating NSE at 23:41
Completed NSE at 23:41, 0.00s elapsed
Nmap scan report for 192.168.1.103
Host is up (0.00027s latency).
Not shown: 977 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.1.154
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
23/tcp open telnet Linux telnetd
25/tcp open smtp Postfix smtpd
|_smtp-commands: metasploitable.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
| ssl-cert: Subject: commonName=ubuntu804-base.localdomain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX
| Issuer: commonName=ubuntu804-base.localdomain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2010-03-17T14:07:45
| Not valid after: 2010-04-16T14:07:45
| MD5: dcd9 ad90 6c8f 2f73 74af 383b 2540 8828
|_SHA-1: ed09 3088 7066 03bf d5dc 2373 99b4 98da 2d4d 31c6
|_ssl-date: 2020-04-21T21:41:09+00:00; 0s from scanner time.
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_RC4_128_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_DES_64_CBC_WITH_MD5
|_ SSL2_DES_192_EDE3_CBC_WITH_MD5
53/tcp open domain ISC BIND 9.4.2
| dns-nsid:
|_ bind.version: 9.4.2
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) DAV/2)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.2.8 (Ubuntu) DAV/2
|_http-title: Metasploitable2 - Linux
111/tcp open rpcbind 2 (RPC #100000)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
512/tcp open exec netkit-rsh rexecd
513/tcp open login
514/tcp open tcpwrapped
1099/tcp open java-rmi GNU Classpath grmiregistry
1524/tcp open bindshell Metasploitable root shell
2049/tcp open nfs 2-4 (RPC #100003)
2121/tcp open ftp ProFTPD 1.3.1
3306/tcp open mysql MySQL 5.0.51a-3ubuntu5
| mysql-info:
| Protocol: 10
| Version: 5.0.51a-3ubuntu5
| Thread ID: 10
| Capabilities flags: 43564
| Some Capabilities: Support41Auth, LongColumnFlag, SupportsTransactions, SupportsCompression, ConnectWithDatabase, SwitchToSSLAfterHandshake, Speaks41ProtocolNew
| Status: Autocommit
|_ Salt: %[yrNmZ[=[2(q%]*TJTK
5432/tcp open postgresql PostgreSQL DB 8.3.0 - 8.3.7
| ssl-cert: Subject: commonName=ubuntu804-base.localdomain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX
| Issuer: commonName=ubuntu804-base.localdomain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2010-03-17T14:07:45
| Not valid after: 2010-04-16T14:07:45
| MD5: dcd9 ad90 6c8f 2f73 74af 383b 2540 8828
|_SHA-1: ed09 3088 7066 03bf d5dc 2373 99b4 98da 2d4d 31c6
|_ssl-date: 2020-04-21T21:41:09+00:00; 0s from scanner time.
5900/tcp open vnc VNC (protocol 3.3)
| vnc-info:
| Protocol version: 3.3
| Security types:
|_ VNC Authentication (2)
6000/tcp open X11 (access denied)
6667/tcp open irc UnrealIRCd
| irc-info:
| users: 1
| servers: 1
| lusers: 1
| lservers: 0
| server: irc.Metasploitable.LAN
| version: Unreal3.2.8.1. irc.Metasploitable.LAN
| uptime: 0 days, 0:10:09
| source ident: nmap
| source host: 257B3328.78DED367.FFFA6D49.IP
|_ error: Closing Link: xrqxienec[192.168.1.154] (Quit: xrqxienec)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
|_ajp-methods: Failed to get a valid response for the OPTION request
8180/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/5.5
MAC Address: 08:00:27:FD:36:7B (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:linux_kernel:2.6
OS details: Linux 2.6.9 - 2.6.33
Uptime guess: 0.004 days (since Tue Apr 21 23:35:38 2020)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=202 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: Hosts: metasploitable.localdomain, irc.Metasploitable.LAN; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_ms-sql-info: ERROR: Script execution failed (use -d to debug)
| nbstat: NetBIOS name: METASPLOITABLE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| METASPLOITABLE<00> Flags: <unique><active>
| METASPLOITABLE<03> Flags: <unique><active>
| METASPLOITABLE<20> Flags: <unique><active>
| WORKGROUP<00> Flags: <group><active>
|_ WORKGROUP<1e> Flags: <group><active>
|_smb-os-discovery: ERROR: Script execution failed (use -d to debug)
|_smb-security-mode: ERROR: Script execution failed (use -d to debug)
|_smb2-time: Protocol negotiation failed (SMB2)
TRACEROUTE
HOP RTT ADDRESS
1 0.27 ms 192.168.1.103
NSE: Script Post-scanning.
Initiating NSE at 23:41
Completed NSE at 23:41, 0.00s elapsed
Initiating NSE at 23:41
Completed NSE at 23:41, 0.00s elapsed
Initiating NSE at 23:41
Completed NSE at 23:41, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.69 seconds
Raw packets sent: 1020 (45.626KB) | Rcvd: 1016 (41.430KB)
(base) [root@FedoraWS ~]#
Is it long enough? Too much even.
This is all on this nmap cheatsheet.
If you find the articles in Adminbyaccident.com useful to you, please consider making a donation.
Use this link to get $200 credit at DigitalOcean and support Adminbyaccident.com costs.
Get $100 credit for free at Vultr using this link and support Adminbyaccident.com costs.
Mind Vultr supports FreeBSD on their VPS offer.